As the effects of the global pandemic are continued to be felt, governments and businesses have been focused on the safety of their citizens, employees and customers.
Meanwhile, cyber attackers are impersonating health organisations and other entities through malicious email campaigns designed to invoke fear. These tactics are done by these attacks so as to create an opportunity to gain access to systems and sensitive information.
In order to protect themselves, organisations should apply a carefully considered approach in proactively addressing cyber challenges during these times. Here are some cyber considerations for organisations as they align their strategies and workforce in relation to the effects of the global pandemic.
Remote working
With more workers shifting to remote working, it has been noticed that the usage of mobile devices and remote access to core business systems has increased. While these new methods are helpful given the restrictions provided by the pandemic, the new working patterns also increase the opportunities for cyber attackers to exploit systems.
This means that taking proactive measures to enable both enhanced user experience and online safety is of paramount importance. By not taking such measures, unprotected devices could lead to the loss of data, privacy breaches, and systems being held at ransom.
Hence, organisations should do the following:
- enforce a consistent layer of multi-factor authentication (MFA) or deploy a step-up authentication depending on the severity of access requests.
- ensure identity and access management processes to fully secure third-party identities access networks.
- have a comprehensive view of privileged identities within their IT environments, including a procedure to detect, prevent, or remove orphaned accounts.
Cyber awareness
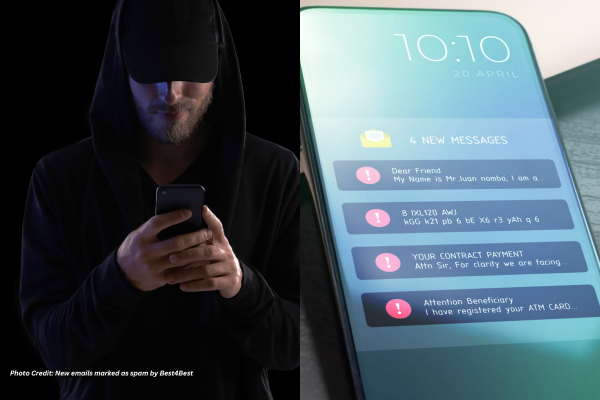
Phishing campaigns related to COVID-19 are increasing. Oftentimes, these phishing campaigns are well disguised to look like they came from reputable health organisations.
These cyber actors would send emails with malicious attachments or links to fraudulent websites to trick victims into revealing sensitive information or donating to fraudulent charities or causes. Attacks like these can propagate quickly and extensively impact an entire enterprise network, cause identity theft and submissions of fraudulent claims for payments and benefit programs.
In order to avoid phishing scams, organisations must advise their employees to do the following:
- exercise caution in handling any email with a COVID-19 related subject line, attachment, or hyperlink, and be wary of social media pleas, texts, or calls related to COVID-19.
- use trusted sources—such as legitimate, government websites for up-to-date, fact-based information about COVID-19.
- refrain from revealing personal or financial information in an email and responding to email solicitations for this information.
Digital transformation
The cyber threat landscape continues to evolve as Australia continues to technologically transform throughout the global pandemic. Likewise, cybercriminals are increasingly looking for new and sophisticated ways to attack operational systems and backup capabilities simultaneously, causing organisation-wide destructive cyberattacks.
To mitigate the impact of these attacks, organisations can improve their defence posture and attack readiness by identifying their “crown jewel assets”, practising good cyber hygiene, reviewing their incident response strategy, architecture and cyber recovery solutions.
Having a viable cyber resiliency program will also help expand the boundaries of traditional risk domains to include new capabilities like employee support services, out-of-band communication and collaboration tools and a cyber recovery vault.
Deloitte also helps organisations strategically prepare for, respond to, recover and transform from high-consequence cyber incidents that could seriously disrupt operations, damage reputation, and destroy shareholder value.
Nonetheless, an organisation’s cyber strategies should converge across business operations, business continuity/technical resilience, and crisis management functions. They should also employ unique methods that reveal network exposures, detection of advanced threats and discovering systemic incident response process gaps.
Source: Ian Blatchford’s Linkedin Page. Content has been edited for style and length.